General Skills
Lets Warm Up
Description
If I told you a word started with 0x70 in hexadecimal, what would it start with in ASCII?
This challenge can be solved in many ways. The easiest is to use an online converter such as RapidTables or CyberChef among others, depending on preference. Simply select the conversion type, and obtain the output. Decoding hex manually is also possible with an ASCII table. These can be found anywhere online.
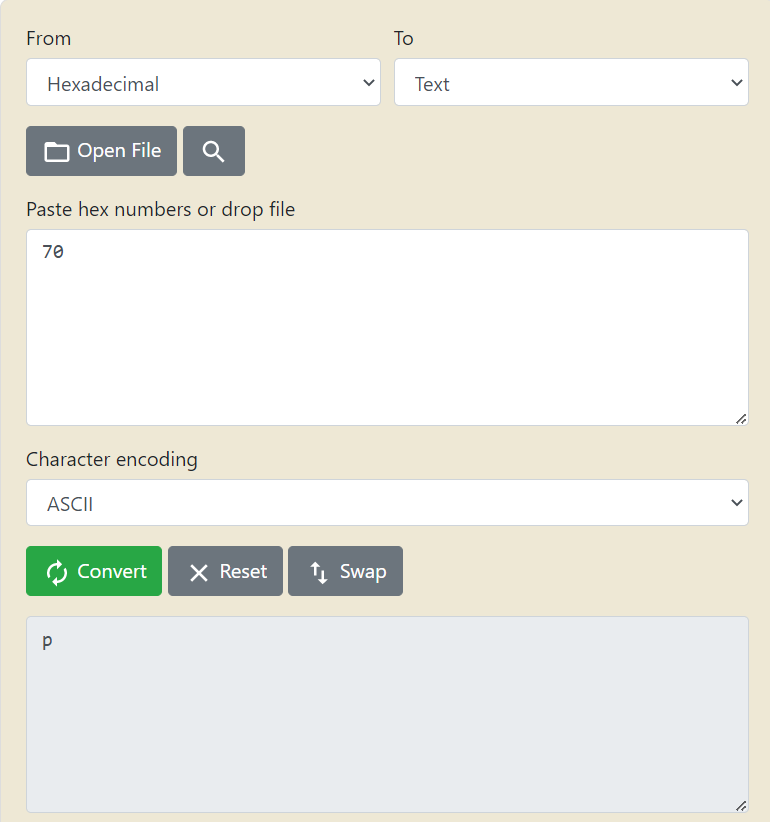
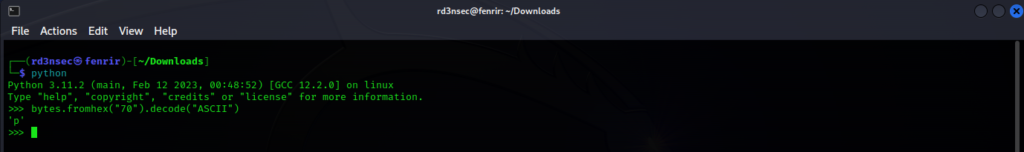
Another solution would be to use Python or Bash if you’re already working with the CLI and either are at your disposal. For Python the command will be: bytes.fromhex("70").decode("ASCII") . For bash use echo, which is used to display a message on screen. The option -e will enable the interpretation of the following backslash-escaped characters like \xHH (Hex): echo -e “\x70”.
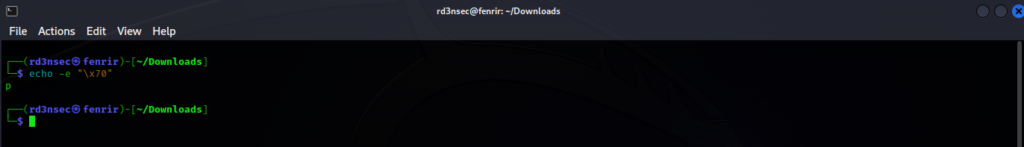
Flag submission:
picoCTF{p}
Warmed Up
Description
What is 0x3D (base 16) in decimal (base 10)?
Once again, this challenge requires an online converter. To use CyberChef simply drag From Hex and To Decimal to the Recipe section. Type in the Hex value you want to convert, in this case: 3D and click the BAKE! button to get the output.
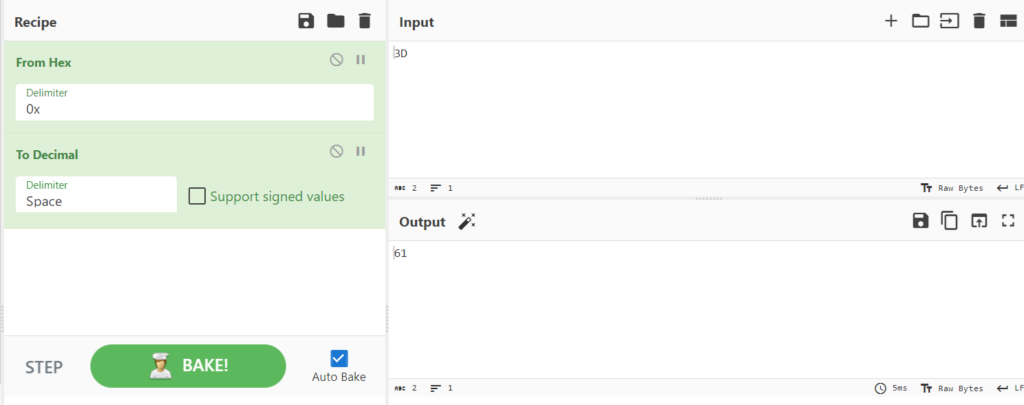
Flag Submission:
picoCTF{61}
2Warm
Description
Can you convert the number 42 (base 10) to binary (base 2)?
We can use an online converter to quickly get the answer to this challenge. However it is also important to know how to complete this conversion manually.
Converting a decimal number to a binary number involves representing the decimal number in base 2 (binary) instead of base 10 (decimal).
Step-by-step guide
- Start with the decimal number you want to convert.
- Divide the decimal number by 2 and note down the quotient (result) and the remainder.
- Continue dividing the quotient by 2 until you reach a quotient of 0. Each time, note down the quotient and remainder.
- Now, write down the remainders you noted earlier in reverse order. This will be your binary representation.
- Pad the binary representation with leading zeros, if necessary, to make it a complete group of 4 or 8 bits (depending on the context).
Convert the decimal number 42 to binary
- Start with 42.
- Divide 42 by 2. The quotient is 21, and the remainder is 0.
- Divide 21 by 2. The quotient is 10, and the remainder is 1.
- Divide 10 by 2. The quotient is 5, and the remainder is 0.
- Divide 5 by 2. The quotient is 2, and the remainder is 1.
- Divide 2 by 2. The quotient is 1, and the remainder is 0.
- Divide 1 by 2. The quotient is 0, and the remainder is 1.
- Now, write down the remainders in reverse order: 11010.
- Since 101010 is already a complete group of 6 bits, we don’t need to pad it with leading zeros.
So, the decimal number 42 in binary is 101010.
Flag Submission:
picoCTF{101010}
Bases
Description
What does this bDNhcm5fdGgzX3IwcDM1 mean? I think it has something to do with bases.
The description for this challenge hints at bases. Often times you may come across long strings of characters that don’t have any apparent meaning at first glance. A good way to figure out the possible encoding, or what base it may be, is to look at the type of characters. The numbers, uppercase, and lowercase letters indicate it may be one of the most common encodings: base64.
By using CyberChef, you can paste the string of characters and use the base 64 encoding. However, there are times when the encoding may not be base64. CyberChef has a “Magic Wand” option where it tries to find an encoding that seems to have meaning in ASCII or Unicode characters.
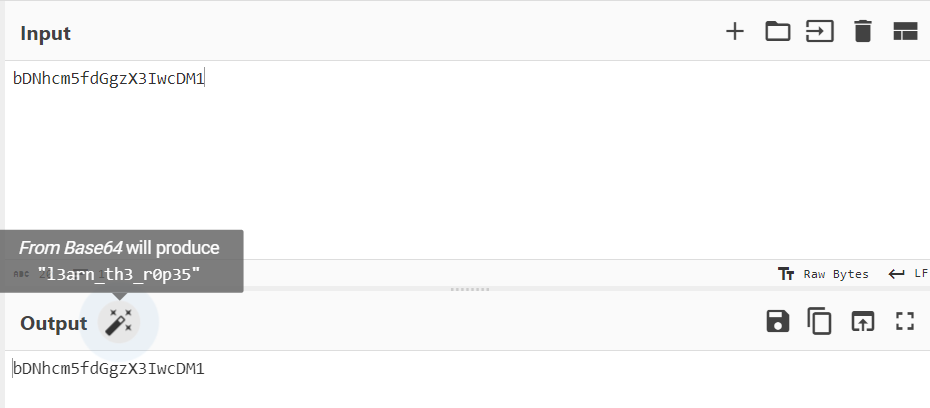
Flag Submission:
picoCTF{l3arn_th3_r0p35}
What’s a net cat?
Description
Using netcat (nc) is going to be pretty important. Can you connect to jupiter.challenges.picoctf.org at port 25103 to get the flag?
Netcat nc is a command-line utility that reads and writes data across network connections, using the TCP or UDP protocols. The most basic syntax of the Netcat utility takes the following form:
nc [options] host port
In order to connect to the host jupiter.challenges.picoctf.org on port 25103 use: nc jupiter.challenges.picoctf.org 25103. You should obtain an immediate response.
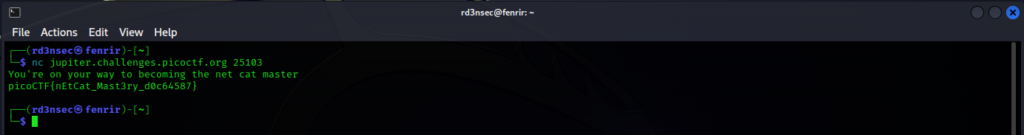
Flag Submission:
picoCTF{nEtCat_Mast3ry_d0c64587}
Strings it
Description
Can you find the flag in file without running it?
This challenge suggests the usage of the command strings, which prints the printable character sequences that are at least 4 characters long and are followed by an unprintable character. What does this mean?
By looking at an ASCII table there are characters that are printable on a computer, such as alphanumeric characters (ABCabc123), standard symbols and punctuation (%(+=$), and whitespace.
Items such as null (NUL), start of heading (SOH), bell (BEL), backspace (BS), etc. are unprintable characters.
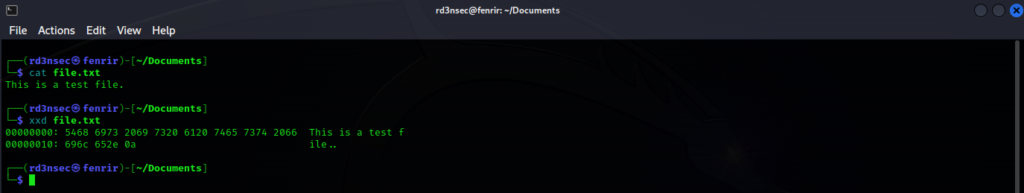
To a computer every file is basically a series of numbers. We can view the same file in a hex dump with the command xxd strings | less. The | less is just so that we get a page by page output and it doesn’t all stream by at once.
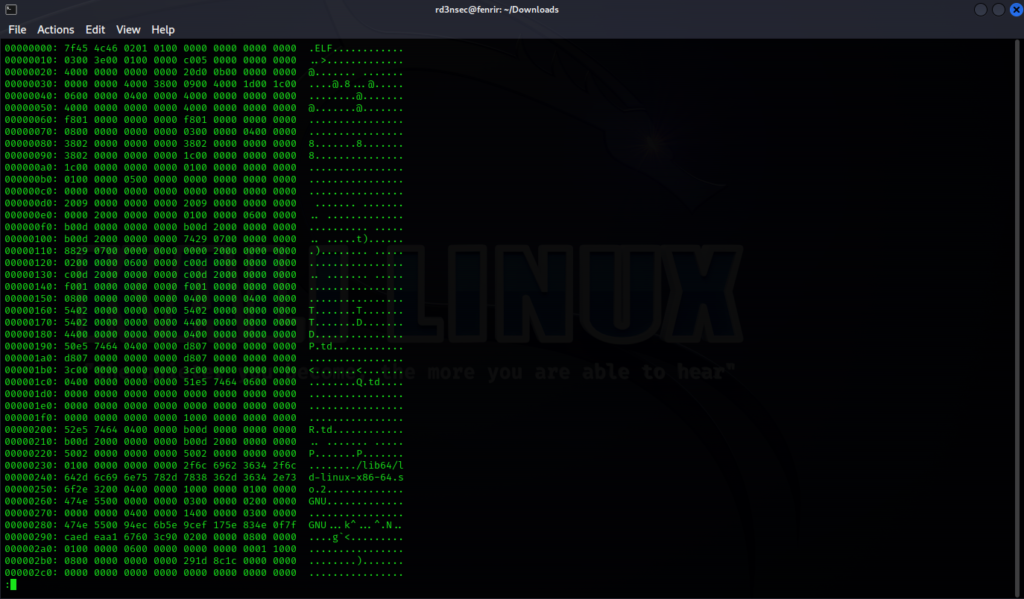
What you are seeing there is the binary contents of the file shown as lines of 8 individual 16-bit values in hexadecimal. The first number on each line is the starting offset in the file for the first of the 8 following values on that line. The middle section is the actual content of the file represented by a series of numbers in hex. The same data can be interpreted as ASCII which is shown on the last section to the right.
Therefore, the command strings runs through all the numbers in the file to check if they are a printable character. If it hits 4 printable characters in a row or more, it will print them out because it could be something meaningful (sometimes it’s just random noise). It will continue to print them out until it reaches an unprintable character.
Finally, to get the flag run the command strings strings, the command followed by the name of the file. However, by running the command as such, we will be met with a lot of plain-text and nonsense which will be quite the hassle to sort through manually. We can follow it with the grep command to filter for specific expressions in plain-text. Since we know the format for the PicoCTF flags is picoCTF{…}, we can grep for picoCTF. The command will look as follows: strings strings | grep picoCTF.
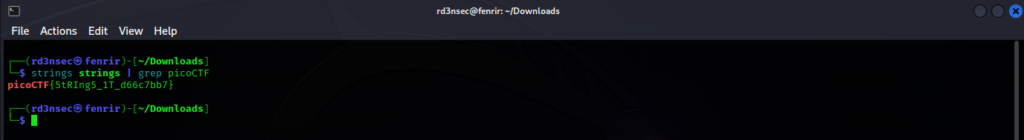
Flag Submission:
picoCTF{5trIng5_1T_d66c7bb7}